Risk Management

- Risk Management
- Risk Identification and Assessment Process
- Business Continuity Plan (BCP)
- Information Security Management System
- Enhancing Information Security Measures
- Information Security Education
- Response to Information Security Incidents
Glory strives to avoid operational risks and mitigate losses in times of disasters, ensuring the safety of stakeholder positions.
Risk Management
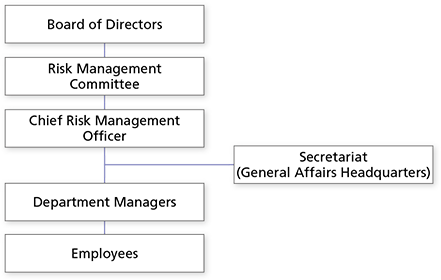
Glory's Risk Management Committee, chaired by the company's president, works to strengthen the Group's risk management based on the risk management framework and process shown below.
In fiscal 2024, the committee conducted group-wide assessment to review risk status and implement measures to mitigate highest priority risks.
Risk Management Framework
The Risk Management Committee manages the Group's risk management framework and is chaired by the company's president.
Risk Identification and Assessment Process
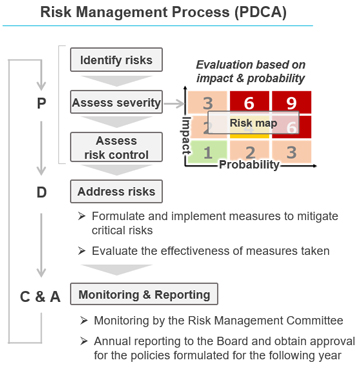
The Glory Group applies the PDCA cycle shown right in its risk management including identification, assessment, and formulation of measures. Identified risks are evaluated on two axes (severity and probability) and high-priority risks are managed by responsible departments which take preventive measures and establish systems to respond promptly in times of crisis. Basic policies, risk management structure, and priority measures for the year are deliberated upon and approved by the Risk Management Committee. Summary of these risk management activities are regularly reported to the company's Board of Directors.
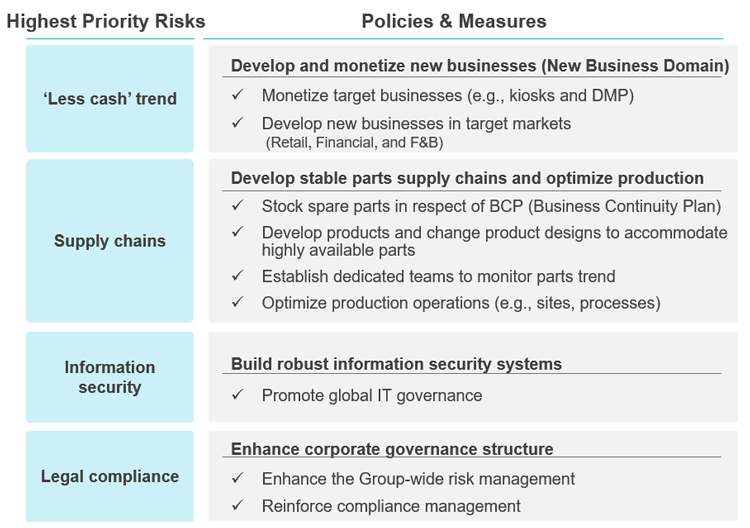
In January 2025, the Risk Management Committee identified the highest priority risks and decided upon the policies and measures as below.
Business Continuity Plan (BCP)

Simulation drill for a machinery oil spill
Glory develops BCPs to prepare for emergencies such as natural disasters and continue its business or/and recover promptly in times of crisis. For stable supplies of products and services in emergency situations, we consistently strengthen our supply chain through diversified parts procurement risks and regular reviews on emergency manuals and regulations. In fiscal 2024, we conducted a tabletop BCP drills at the Himeji Headquarters. Our domestic subsidiaries with production functions also carried out BCP drills based on specific disaster scenarios.
We also enhance our countermeasures against network damage that is critical to our business continuity. For example, we have expanded the coverage of safety confirmation system, installed satellite phones at major business locations, and stockpiled supplies of food and water for contingencies. We regularly evaluate the effectiveness of these countermeasures through disaster drills.
Information Security Management System
Glory handles a large volume of confidential information concerning matters such as cash processing and settlement processing. Accordingly, we focus on the integrated strengthening of our information security throughout the Group based on the Information Security Basic Policy and Privacy Policy, which stipulate our basic stance and attitude as a Group.
Measures for Organizational Safety Management
Under the supervision of the Chief Information Security Officer (Group CISO), we have established the Information Security Promotion Section as a company-wide cross-sectional organization to improve the level of information security for the entire Group. The section has been making continuous improvements through the PDCA cycle based on the Information Security Policy. Internal audits are also conducted regularly to check the suitability and effectiveness of the system. In addition, as a measure to strengthen security not only for the Group but also for the entire supply chain, we conduct security surveys of contractors who handle important information to ascertain their security levels and provide guidance on improvements as necessary.
Enhancing Information Security Measures
For the purpose of safely and appropriately handling the information assets of our customers, departments concerned with offering systems solutions and services, such as the Service Connect Center (Information processing center), have acquired ISO 27001 certification, the international standard for information security.
Business sites and departments that have acquired ISO 27001 certification
| GLORY LTD. | Service Connect Center, System Development Division, Glory Monitoring Center, DX Innovation Development Department |
|---|---|
| Domestic group companies | GLORY Technical Solutions Ltd. SC Business Division (Former GLORY System Create Ltd.), GLORY NASCA Ltd. |
| Overseas group companies | Sitrade Italia S.p.A. |
Technical Safety Management
We strengthen information security through ID management systems and intrusion prevention systems that prevent unauthorized entries via the internet or limit the use of external storage through device control. In addition, we implement two-factor authentication for data integration platforms to prevent unauthorized use by third parties.
For remote workers, we provide VPN (Virtual Private Network) connections to ensure network security and prevent the leakage of confidential information. Additionally, we enhance endpoint security through vulnerability management, anti-virus software, MDM (Mobile Device Management System), and EDR (Endpoint Detection and Response) solutions.
Physical Safety Management
We have introduced an entrance and exit management system with ID cards or facial recognition along with a key management system to strictly control access and automatically save records.
We also ensure the continuous operation of the IT infrastructure by installing equipment such as private power generators and a UPS (uninterruptible power system).
Information Security Education
Personnel Safety Management
We respond to constantly changing technologies and social circumstances and conduct level-based employee training to prevent information security breaches.
Our training includes programs for new employees to provide them with a basic knowledge of information security and relevant laws and regulations and training on supervisor responsibilities for information security so management can acquire the knowledge they need. We also conduct training programs for managementlevel personnel to deepen understanding of social trends (external environment) and our status (internal environment) related to information security.
We also conduct an annual, group-wide e-learning program in October during Corporate Ethics Month to strengthen the information security literacy of employees. Due to the increased the risk of information leaks from telework, we provide employees with training on risk prevention compliance.
Response to Information Security Incidents
In preparation for information security incidents such as data leaks, malware infection, and unauthorized access, we have established a system for minimizing damage, promptly recovering and preventing reoccurrence. G-CSIRT (Glory Computer Security Incident Response Team), which plays a central role in this effort, joined Nippon CSIRT Association, an industry group, in 2014 and has been enhancing response capabilities to incidents through such initiatives as gathering and sharing information and acquiring related skills. The system is being further strengthened to enhance the response to incidents in products, services and at offices.



